Overview of security model implemented in Enterprise Bridge, which ensures exceptional protection for your data on all stages of digital transformation process.
Secure on-premise solution
Enterprise Bridge is installed on migration server inside client's perimeter and never connects outside of it for whatever purpose. It is fully isolated on-premise solution, which complies to highest security requirements. Enterprise Bridge does not need any third party or cloud components to be installed or configured. On-premise application provides exceptional data security and control...
Direct data pipe transfer
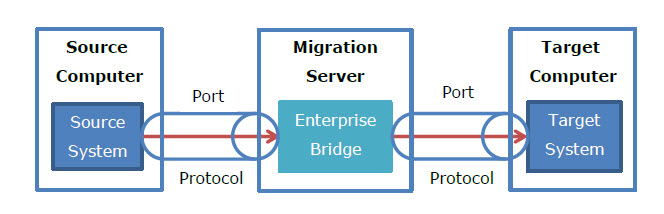
Migration architecture is very simple and only includes interaction of Enterprise Bridge with data source and data target. Each part of this combination and communication between these parts can be secured by best possible means. Enterprise Bridge implements direct data pipeline. It is a system for retrieving data from various sources and funneling it into...
No middle-ware storage

Usually Enterprise Bridge does not store data on migration server. It does not include and does not require any internal or external database system. It is just a pipe for data transfer and transformation between source and target system. The data flow directly from source to target system through secure data pipeline. Occasional fragments and...
No third-party dependencies

One can say that Enterprise Bridge itself does not have any architecture at all. It is just singular application built entirely on Microsoft© .NET Framework and executed by authorized user of Microsoft© Windows. Enterprise Bridge does not use any third party components, such as databases of cloud services for its operation. Machine where Enterprise Bridge...
No cloud components

Enterprise Bridge itself never connects outside for whatever purpose, except for connection to data source and data target. Enterprise Bridge does not use any external hosts or ports for its own operation. Firewall rules must include only addresses and ports of source and target systems intended for migration. Which address, protocol and port must be...
Most advanced security protocols

Enterprise Bridge from its side offers most secure environment for data transfer. It supports most secure means of communication and protocols supported by each data system. Data administrators should always configure their systems in most secure way, as far as it is possible. For outdated, insecure or compromised systems Enterprise Bridge offers unique security advantage...
Custom SSO procedures
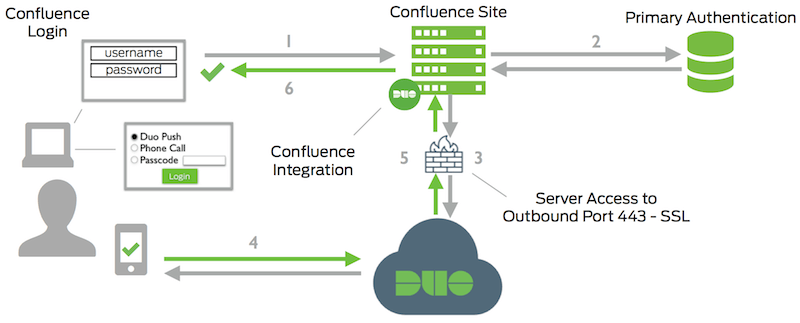
Many companies implement custom SSO procedures to secure their data. Enterprise Bridge transparently supports most of third-party and custom SSO systems through unique adaptive logon sequences. Single sign-on (SSO) is a session and user authentication service that permits a user to use one set of login credentials -- for example, a username and password -...
Access through API tokens
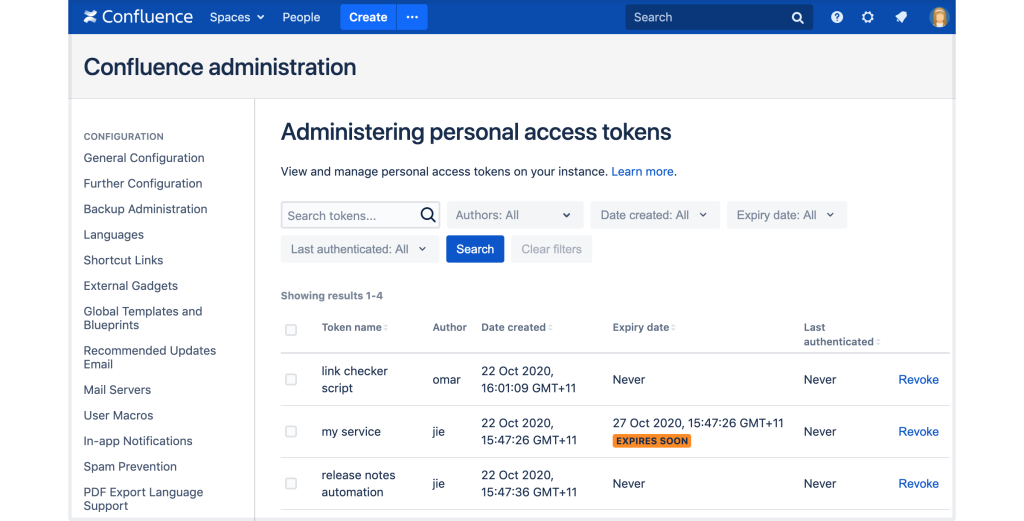
Enterprise Bridge supports secure access through API tokens on all client systems where they are implemented. For example token authorization is recommended and secure way to access Confluence and JIRA servers. Personal access tokens (PATs) are a secure way to use scripts and integrate external applications with your Atlassian application. If an external system is...